In the news
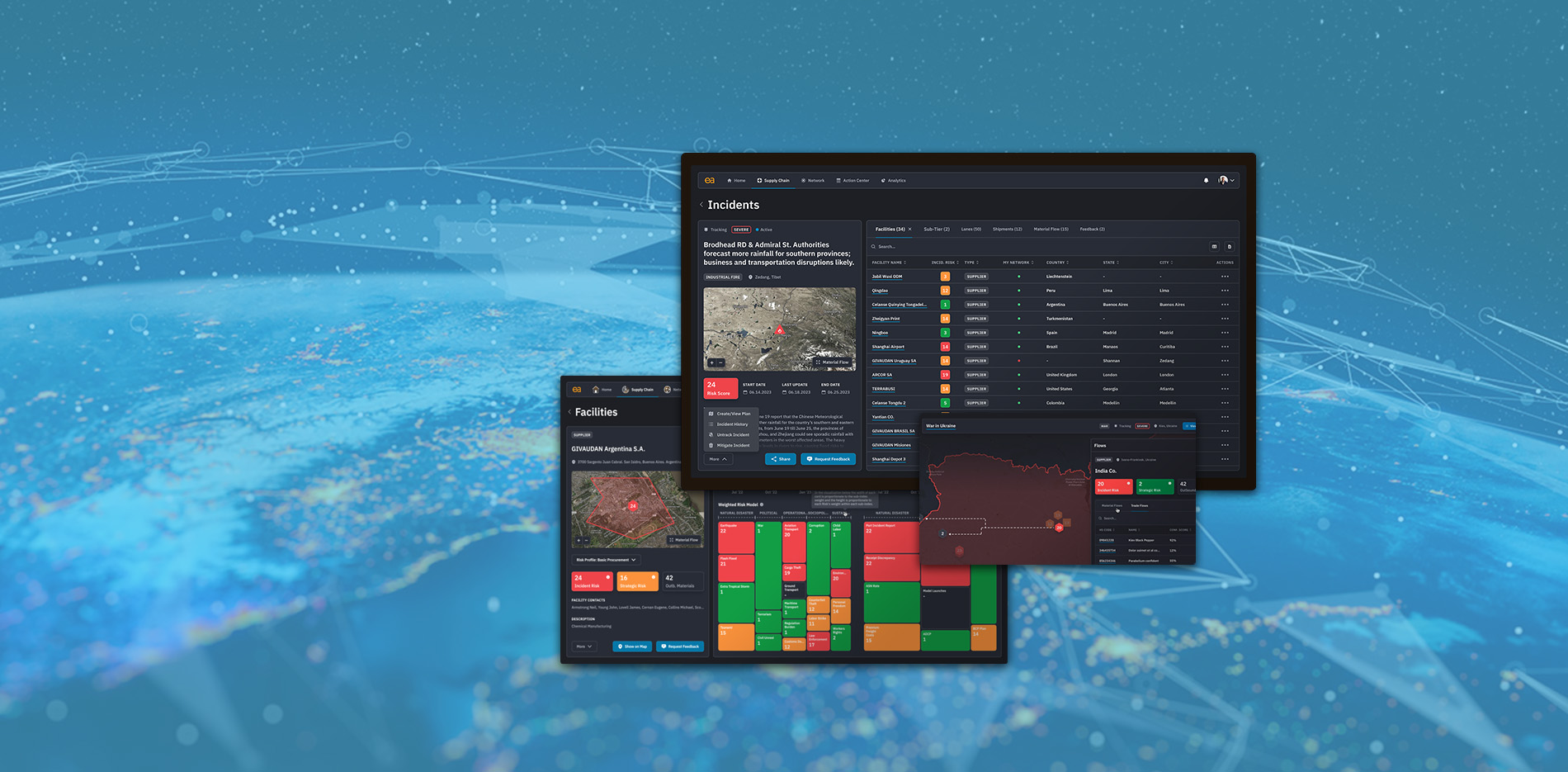
Go beyond standard supply chain risk management

If you had 4 months' notice...
what could you do differently?
Get the predictive insights and risk analytics to make your global supply chain faster, smarter, leaner, and more sustainable
Request a demoInsights and Improvements
Let’s call this qualitative quantity
At Everstream, we’re helping customers build a better, more autonomous supply chain. Here’s how they’re proving it.
partnerships that last
The best trust the best
Our clients trust us to make their supply chains smarter and more autonomous.
Explore helpful blogs, webinars, research and other content from our global experts
Everstream’s white paper shares how AI-managed data cleansing and integration improves port performance, increases revenue, enhances competitive advantage, and ensures operational resilience.
In 2024, volatile supply chains challenge businesses, highlighting the need for improved visibility and comprehensive risk management. Our webinar uncovers strategies and best practices, including a live demo of Everstream’s AI-powered sub-tier visibility solution, to safeguard supply chains and business value.